You are currently viewing the content available in Vietnam. If you are looking for information for another region, please select the correct country from the top-left dropdown in the page and 'Navigate to Browse FAQs' in the Support menu.
Issue
Managing Users within StruxureWare Data Center Expert
Product Line
StruxureWare Data Center Expert (DCE)
InfraStruXure Central (ISXC)
Environment
StruxureWare Data Center Expert (all versions)
StruxureWare Central (all versions)
InfraStruXure Central (all versions)
Active Directory (AD) or OpenLDAP Authentication Server
Resolution
Local Users
Managing Local Users
Local: Creating Users
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
3) Fill in the required/necessary user information.
4) If you would like the user to be part of a group, select the group within the User Group membership tab.
Local: Creating User Groups
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click Add User Group...
3) Fill in the required/necessary User Group information.
4) Click the User Group Members tab.
5) Select (checked box) the Users that should be part of this group.
Local: Editing a User or User Group
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Select (left-click once) a user or user group from the list and click Edit.
3) Edit the necessary information.
4) Click OK to save the changes.
Local: Deleting Users / User Groups
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Select (left-click once) the User or User Group.
3) Click Delete.
4) Confirm the username and click Yes to delete the user.
Local: Editing User or User Group Access Permissions
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click Device Group Access.
3) Select (left-click once) the user or user group within the left pane.
4) Select (left-click once) a device group in the right pane.
5) Click Modify Device Group Access.
6) Select the desired radial buttons for Monitoring Access and Surveillance Access.
7) Click OK to save the changes.
Managing Remote Users
Remote: Adding an Authentication Server and Users/Groups
1) Define a user within your AD/OpenLDAP server that will be used to make the connection.
3) Click the Authentication Servers tab.
4) Click Add Authentication Server...
9) Check the boxes next to the users and user groups. Select Finish.
Please ensure to reference Data Center Expert | Tips for configuring Active Directory integration for further troubleshooting and guidance. Note for port 636 connections: DCE does not support wildcard certificates. The hostname of the server has to be the common name on the certificate if they do not match in any capacity it will fail.
AD/LDAP Remote Users cannot be added to Local Groups
AD/LDAP Search Base may be Too Large
AD/LDAP Users and User Groups must be within the same search base
Active Directory Users must login using Pre-Windows 2000 Usernames
Active Directory Group Type
Issues Binding to Search Base that Contains an Object starting with #
Protected Users
Users can no longer log into DCE after changing Active Directory or OpenLDAP structure.
Unable to remove Active Directory Groups (Authentication Server Offline)
"Unable to Reach Host" message during Authentication Server Configuration
After upgrading to 7.8.0.46, users that are added via Active Directory groups can no longer authenticate.
Managing Users within StruxureWare Data Center Expert
Product Line
StruxureWare Data Center Expert (DCE)
- Basic Appliance (AP9465)
- Standard Appliance (AP9470)
- Enterprise Appliance (AP9475)
- Virtual Appliance (AP94VMACT)
StruxureWare Central (SWC)- Standard Appliance (AP9470)
- Enterprise Appliance (AP9475)
- Virtual Appliance (AP94VMACT)
InfraStruXure Central (ISXC)
Environment
StruxureWare Data Center Expert (all versions)
StruxureWare Central (all versions)
InfraStruXure Central (all versions)
Active Directory (AD) or OpenLDAP Authentication Server
Resolution
Local Users
- Creating Users
- Deleting Users
- Creating a User Group
- Editing a User or User Group
- Editing User or User Group Access Permissions
Remote Users - Deleting Users
- Creating a User Group
- Editing a User or User Group
- Editing User or User Group Access Permissions
- Adding an Authentication Server and Users/Groups
- Adding/Removing Users and User Groups within an already added Authentication Server
- Editing User or User Group Access Permissions
- Deleting an Authentication Server
Additional Information / Troubleshooting / Known Issues- Adding/Removing Users and User Groups within an already added Authentication Server
- Editing User or User Group Access Permissions
- Deleting an Authentication Server
Managing Local Users
Local: Creating Users
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
NOTE: Shows you the local and remote users that have been added into DCE. By default there is only the local apc user.
2) Click Add User...3) Fill in the required/necessary user information.
4) If you would like the user to be part of a group, select the group within the User Group membership tab.
NOTE: A user does not have to be added to any groups. This is an option step that may help manage permissions for multiple users.
5) Click OK to create the user. Local: Creating User Groups
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click Add User Group...
3) Fill in the required/necessary User Group information.
4) Click the User Group Members tab.
5) Select (checked box) the Users that should be part of this group.
Local: Editing a User or User Group
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Select (left-click once) a user or user group from the list and click Edit.
3) Edit the necessary information.
4) Click OK to save the changes.
Local: Deleting Users / User Groups
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Select (left-click once) the User or User Group.
3) Click Delete.
4) Confirm the username and click Yes to delete the user.
Local: Editing User or User Group Access Permissions
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click Device Group Access.
3) Select (left-click once) the user or user group within the left pane.
4) Select (left-click once) a device group in the right pane.
5) Click Modify Device Group Access.
6) Select the desired radial buttons for Monitoring Access and Surveillance Access.
7) Click OK to save the changes.
Managing Remote Users
Remote: Adding an Authentication Server and Users/Groups
1) Define a user within your AD/OpenLDAP server that will be used to make the connection.
NOTE: It is recommended that this user is set with a password that does not expire. If the password expires, no users that are authenticated through the connection that uses the expired credentials will be able to login. A local administrator user would need to be used to change the password for the bind user.
2) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.3) Click the Authentication Servers tab.
4) Click Add Authentication Server...
- Provide a label for the AD server.
- Enter the IP Address of the AD server.
- Select the Server Type.
- Click Next.
5) Enter the Bind User DN, which is the full path to bind user within the authentication server structure. - Enter the IP Address of the AD server.
- Select the Server Type.
- Click Next.
- The bind user DN is required to be entered with specific syntax, which is case sensitive. EX: cn=bind-user,cn=Users,dc=dcim,dc=apc,dc=com
- It is recommended to user a service account for this configuration. You may also elect to have a password that does not expire for this user in AD or your users may get locked out of the application until resolved.
- See Determining Bind User DN for details on how to obtain this value.
- It is recommended to user a service account for this configuration. You may also elect to have a password that does not expire for this user in AD or your users may get locked out of the application until resolved.
- See Determining Bind User DN for details on how to obtain this value.
6) Enter the Bind User Password, which is the password of the Bind User defined within Step 5.
7) Enter the Search Base where the users and groups are located within the AD/LDAP authentication server. NOTE: The search base is required to be entered with specific syntax, which is case sensitive. EX: dc=dcim,dc=apc,dc=com
NOTE: If you are going to be adding an AD/LDAP group, the group(s) and users must be located within the search base.
- See Determining Search Base for details on how to obtain this value.
8) Click Next.- See Determining Search Base for details on how to obtain this value.
9) Check the boxes next to the users and user groups. Select Finish.
NOTE: If using groups, you do not need to select the individual users.
10) Click Finish to add the Authentication Server.
Remote: Adding/Deleting Users and User Groups within an already added Authentication Server
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click the Authentication Servers tab.
3) Select (left-click once) the Authentication Server.
4) Click Edit Authentication Server.
5) Click Next twice.
6) Select (checked box) or Deselect (unchecked box) the users and user groups.
7) Click Finish to finish the user additions/removals.
Remote: Editing User or User Group Access Permissions
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click Device Group Access.
3) Select (left-click once) the remote user or remote user group within the left pane.
4) Select (left-click once) a device group in the right pane.
5) Click Modify Device Group Access.
6) Select the desired radial buttons for Monitoring Access and Surveillance Access.
7) Click OK to save the changes.
Remote: Deleting an Authentication Server
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click Authentication Servers tab.
3) Select (left-click once) the Authentication Server.
4) Click Delete.
5) Confirm the Authentication Server and click Yes to delete the Authentication Server.
Remote: Determining Bind User DN
1) Open Windows Powershell and run the following command, ensuring to replace "binduser" with the username of the user you want to use to connect to the Active Directory server.
Example Result:
Remote: Determining Search Base
1) Open Windows Powershell and run the following command, ensuring to replace "OU_Name" with the Organization Unit Name of the user you want to use to connect to the Active Directory server.
Example Result:

Additional InformationRemote: Adding/Deleting Users and User Groups within an already added Authentication Server
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click the Authentication Servers tab.
3) Select (left-click once) the Authentication Server.
4) Click Edit Authentication Server.
5) Click Next twice.
6) Select (checked box) or Deselect (unchecked box) the users and user groups.
7) Click Finish to finish the user additions/removals.
Remote: Editing User or User Group Access Permissions
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click Device Group Access.
3) Select (left-click once) the remote user or remote user group within the left pane.
4) Select (left-click once) a device group in the right pane.
5) Click Modify Device Group Access.
6) Select the desired radial buttons for Monitoring Access and Surveillance Access.
7) Click OK to save the changes.
Remote: Deleting an Authentication Server
1) Within the DCE Desktop Client navigate to the System Menu and select Users and Device Group Access.
2) Click Authentication Servers tab.
3) Select (left-click once) the Authentication Server.
4) Click Delete.
5) Confirm the Authentication Server and click Yes to delete the Authentication Server.
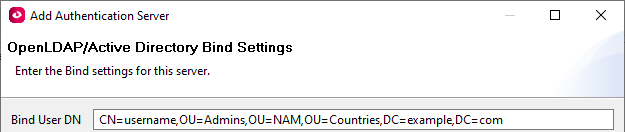
Remote: Determining Bind User DN
1) Open Windows Powershell and run the following command, ensuring to replace "binduser" with the username of the user you want to use to connect to the Active Directory server.
Get-ADUser -Identity binduser | select DistinguishedNameIf you receive an error you likely need to download and install RSAT (Remote Server Administration Tools) from Microsoft: https://www.microsoft.com/en-us/download/details.aspx?id=45520
Example Result:
DistinguishedName ----------------- CN=username,OU=Admins,OU=NAM,OU=Countries,DC=example,DC=com3) Example Bind User DN from step 2 to enter into Bind User DN field:
Remote: Determining Search Base
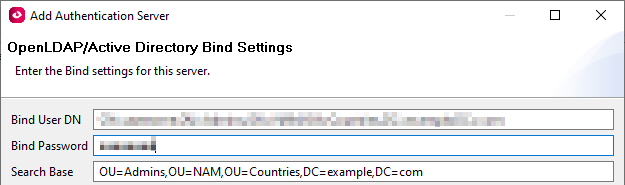
1) Open Windows Powershell and run the following command, ensuring to replace "OU_Name" with the Organization Unit Name of the user you want to use to connect to the Active Directory server.
Get-ADOrganizationalUnit -Filter 'Name -like "OU_Name"' | select DistinguishedNameIf you receive an error you likely need to download and install RSAT (Remote Server Administration Tools) from Microsoft: https://www.microsoft.com/en-us/download/details.aspx?id=45520
Example Result:
DistinguishedName ----------------- OU=Admins,OU=NAM,OU=Countries,DC=example,DC=com3) Once a result is obtained, the Bind User DN should be the full result.
Please ensure to reference Data Center Expert | Tips for configuring Active Directory integration for further troubleshooting and guidance. Note for port 636 connections: DCE does not support wildcard certificates. The hostname of the server has to be the common name on the certificate if they do not match in any capacity it will fail.
AD/LDAP Remote Users cannot be added to Local Groups
- In order to define permissions on a group scale with Remote Users and Remote User Group, defined within the AD/LDAP servers, must be used. Adding remote users to local user groups is not supported. This is working as designed.
AD/LDAP Search Base may be Too Large
- If only some remote users are able to login or binding during configuration takes too long (or produces an error) the search base may be too large.
- DCE supports search bases up to 10000 objects, including: Users, User Groups, Containers, etc.
- Multiple authentication servers can be created if the authentication server setup allows. Within each respective authentication server entry, the users and user groups must be in that respective search base.
- DCE supports search bases up to 10000 objects, including: Users, User Groups, Containers, etc.
- Multiple authentication servers can be created if the authentication server setup allows. Within each respective authentication server entry, the users and user groups must be in that respective search base.
AD/LDAP Users and User Groups must be within the same search base
- AD/LDAP users and user groups must exist within the same search base. If the users are located outside of the search base, they will be unable to authenticate, even if the user group has been selected within the authentication server settings. To correct the issue, ensure the search base includes both the users and user groups. This is working as designed.
Active Directory Users must login using Pre-Windows 2000 Usernames
- Users must login using the Pre-Windows 2000 username (found within the Properties of the User Object in Active Directory).
- The syntax of the user may be slightly different that the username used to log into other systems.
- The username case must be used exactly as shown within the Pre-Windows 2000 username.
- If there is a space within the username, try to log using quotes around the username, EX: "John Smith"
- The syntax of the user may be slightly different that the username used to log into other systems.
- The username case must be used exactly as shown within the Pre-Windows 2000 username.
- If there is a space within the username, try to log using quotes around the username, EX: "John Smith"
Active Directory Group Type
- If adding User Groups from Active Directory instead of individual user objects, the User Group CANNOT be a Global Group. Change the User Group type to Universal to resolve the issue.
Issues Binding to Search Base that Contains an Object starting with #
- AD objects that begin with a # can cause parsing issues within DCE. You will see an error if this happens that states 'Invalid Attribute.' Typically binding to a Search Base one container higher than the one that contains the object beginning with '#' will resolve the issue. However, you cannot select any AD Objects within the container that also contains the '#' object.
Protected Users
- Windows 8.1 and Windows Server 2012 R2 have a Protected Users group. As of DCE 7.4.1, adding a user that is also a member of this group will cause authentication to fail.
- More information on Protected Groups: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/dn466518(v=ws.11)
- More information on Protected Groups: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/dn466518(v=ws.11)
Users can no longer log into DCE after changing Active Directory or OpenLDAP structure.
- DCE records the specific structure of the authentication server search base. You will need to remove and re-add the AD/LDAP user/group within the authentication server settings. This is working as designed.
Unable to remove Active Directory Groups (Authentication Server Offline)
- If the configured AD/OpenLDAP server goes offline or is decommissioned before the Authentication Server is removed from DCE, the groups added through the authentication server may not be able to be deleted. If possible, put the active directory user back on-line to process the deletion. Once communication can occur between the two systems, the Authentication Server entry can be removed.
- If the server cannot be brought back online with the same IP or server name, contact your local technical support for assistance.
- If the server cannot be brought back online with the same IP or server name, contact your local technical support for assistance.
"Unable to Reach Host" message during Authentication Server Configuration
- The error indicates that the client is unable to access the remote Authentication Server at the address/port provided.
- The client computer must have access on the network to the Authentication server as it is performing the connection during the configuration.
- When the configuration is finished the DCE appliance will connect to the Authentication Server(s) for user verification. The Client to Authentication Server connection is only used during configuration of the Authentication Server.
- The client computer must have access on the network to the Authentication server as it is performing the connection during the configuration.
- When the configuration is finished the DCE appliance will connect to the Authentication Server(s) for user verification. The Client to Authentication Server connection is only used during configuration of the Authentication Server.
- This message is not logged in any DCE client or Server logs.
After upgrading to 7.8.0.46, users that are added via Active Directory groups can no longer authenticate.
There was an issue that prevented users that are added to Data Center Expert via an Active Directory group from authenticating. This issue has been corrected in version 7.8.0.47, but at this time there is no fix for users that have already upgraded to 7.8.0.46. This issue is being actively worked on by development for a fix to the 7.8.0.46 version. The only current work around is that the users can be individually added into Data Center Expert via Active Directory, instead of using Groups.
Released for:Schneider Electric Vietnam











